Amazon Kinesis source
This event source acts as a consumer of an Amazon Kinesis Data Stream and forwards all messages it reads after wrapping them in a CloudEvent envelope.
With tmctl:
tmctl create source awskinesis --arn <arn> --auth.credentials.accessKeyID <keyID> --auth.credentials.secretAccessKey <key>
On Kubernetes:
apiVersion: sources.triggermesh.io/v1alpha1
kind: AWSKinesisSource
metadata:
name: sample
spec:
arn: arn:aws:kinesis:us-west-2:123456789012:stream/triggermeshtest
auth:
credentials:
accessKeyID:
valueFromSecret:
name: awscreds
key: aws_access_key_id
secretAccessKey:
valueFromSecret:
name: awscreds
key: aws_secret_access_key
sink:
ref:
apiVersion: eventing.triggermesh.io/v1alpha1
kind: RedisBroker
name: triggermesh
When TriggerMesh is running on Amazon EKS, you can use an IAM role for authentication rather than an access key and secret. In this case, TriggerMesh will generate a Kubernetes service account for you that will leverage this IAM role. You also have the option of specifying your own service account name, and if a service account with the same name already exists and it is already managed by the TriggerMesh controller, then it will be reused. By reusing the same serivce account in this way, you can avoid having to create many STS trust relationships for each generated service account.
For more details on authenticating with AWS, please take a look at our dedicated guide on AWS credentials.
Events produced have the following attributes:
- type
com.amazon.kinesis.stream_record - Schema of the
dataattribute: com.amazon.kinesis.stream_record.json
See the Kubernetes object reference for more details.
Prerequisite(s)
- Kinesis Data Stream
- Amazon Resource Name (ARN)
- API Credentials
Kinesis Data Stream
If you don't already have an Amazon Kinesis Data Stream, create one by following the instructions at Creating and Updating Data Streams.
Amazon Resource Name (ARN)
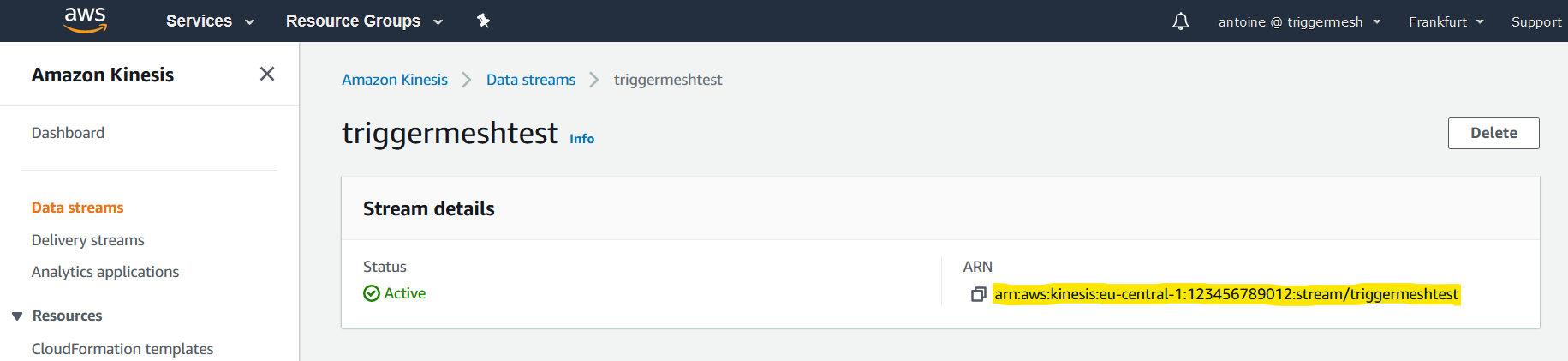
A fully qualified ARN is required to uniquely identify the Amazon Kinesis Stream.
This ARN can be obtained directly from the overview page of the Kinesis Stream. It typically has the following format:
Alternatively, one can obtain the ARN of a Kinesis Stream by using the AWS CLI. The following command
retrieves the information of a stream called triggermeshtest in the us-west-2 region:
$ aws kinesis describe-stream --stream-name triggermeshtest --region us-west-2
{
"StreamDescription": {
"StreamARN": "arn:aws:kinesis:us-west-2:123456789012:stream/triggermeshtest",
"StreamName": "triggermeshtest",
"StreamStatus": "ACTIVE",
(...)
}
}
API Credentials
The TriggerMesh event source for Amazon Kinesis authenticates calls to the AWS API using AWS Access Keys. The page Understanding and getting your AWS credentials contains instructions to create access keys when signed-in either as the root user or as an IAM user. Take note of the Access Key ID and Secret Access Key, they will be used to create an instance of the event source.
It is considered a good practice to create dedicated users with restricted privileges in order to programmatically access AWS services. Permissions can be added or revoked granularly for a given IAM user by attaching IAM Policies to it.
As an example, the following policy contains only the permissions required by the TriggerMesh Amazon Kinesis event source to operate:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"kinesis:DescribeStream",
"kinesis:GetShardIterator",
"kinesis:GetRecords"
],
"Resource": "arn:aws:kinesis:*:*:*"
}
]
}