Splunk target
Sends events to a Splunk HTTP Event Collector (HEC).
With tmctl:
On Kubernetes:
apiVersion: targets.triggermesh.io/v1alpha1
kind: SplunkTarget
metadata:
name: sample
spec:
endpoint: https://mysplunk.example.com:8088
token:
valueFromSecret:
name: splunk-hec
key: token
- Endpoint: URL of the HTTP Event Collector (HEC). Only the scheme, hostname, and port (optionally) are evaluated. When the URL path is not present, the one documented at Splunk is automatically used.
- Token: Contains a token for authenticating requests against the HEC, as discussed in the prerequisites.
- Index: Name of the index to send events to. When undefined, events are sent to the default index defined in the HEC token's configuration.
You can use the optional discardCloudEventContext parameter to omit CloudEvents context attributes from the event written to Splunk. When this property is false (default), the entire CloudEvent payload is included. When this property is true, only the CloudEvent data is included.
Accepts events of any type. See the Kubernetes object reference for more details.
Prerequisite(s)
- Enable HTTP Event Collector Input
- HEC token
Open the Splunk web console, then navigate to Settings > Data > Data inputs.
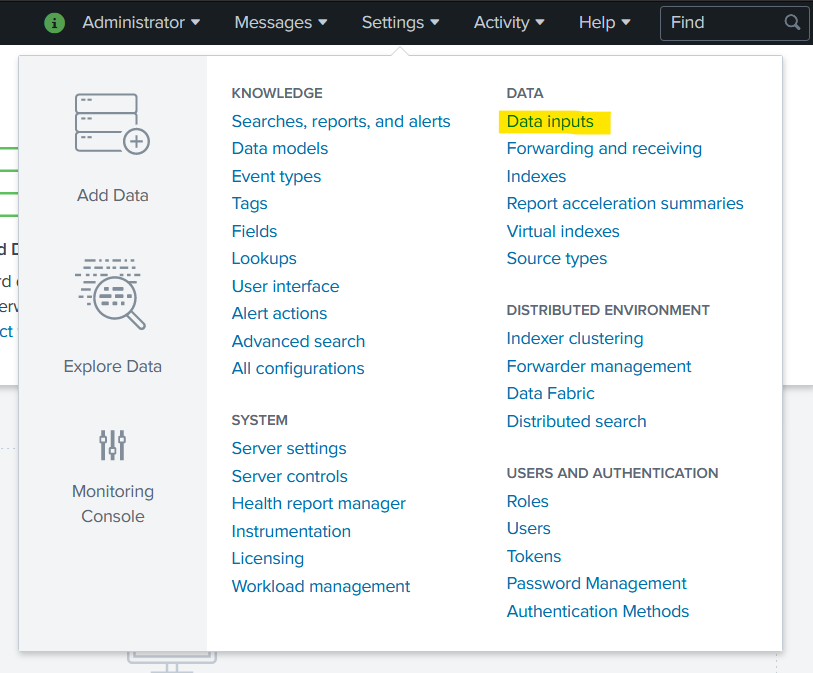
In the list of local inputs, click HTTP Event Collector.
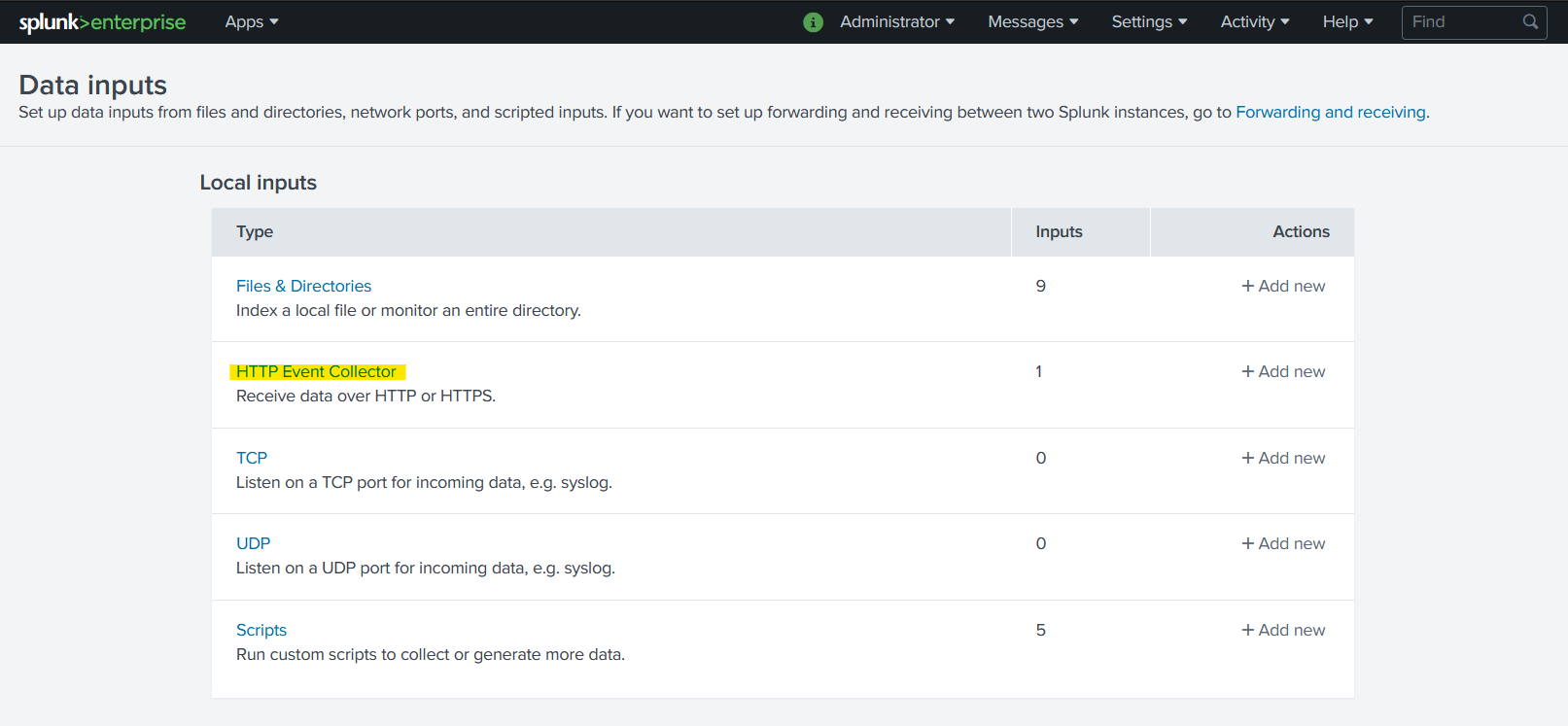
Click New token in order to generate a new token with custom settings, then take note of the value of that token. The
default HEC token (splunk_hec_token) is also suitable for use with the TriggerMesh event Target for Splunk.
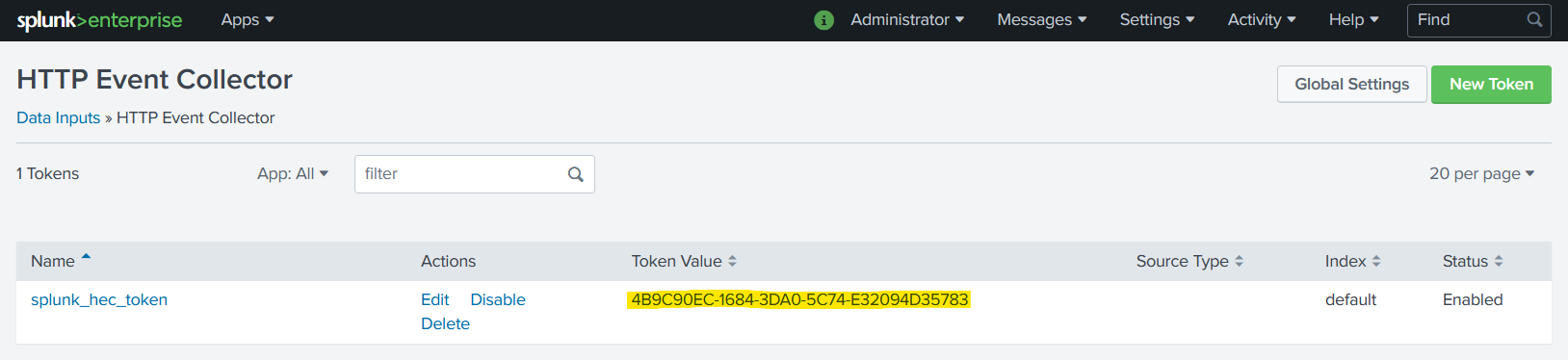
This procedure is described in more detail in the Splunk documentation: Set up and use HTTP Event Collector in Splunk Web.
To check if you Splunk Target is working, new events should be visible in the Search & Reporting app inside Splunk.
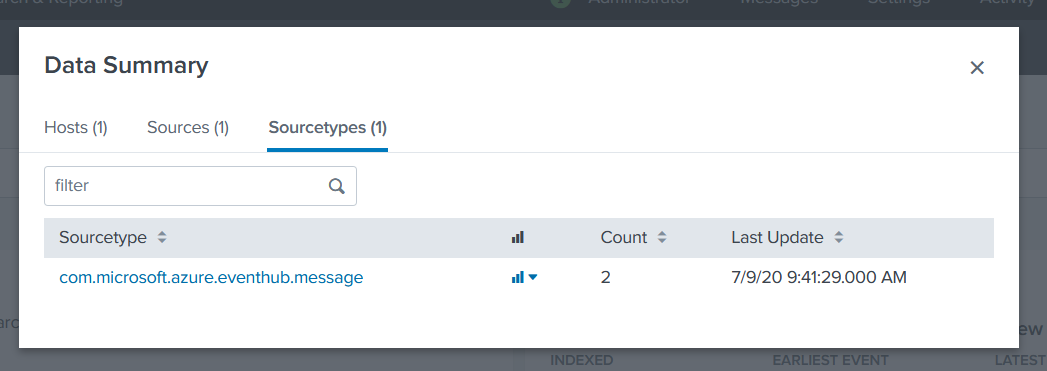
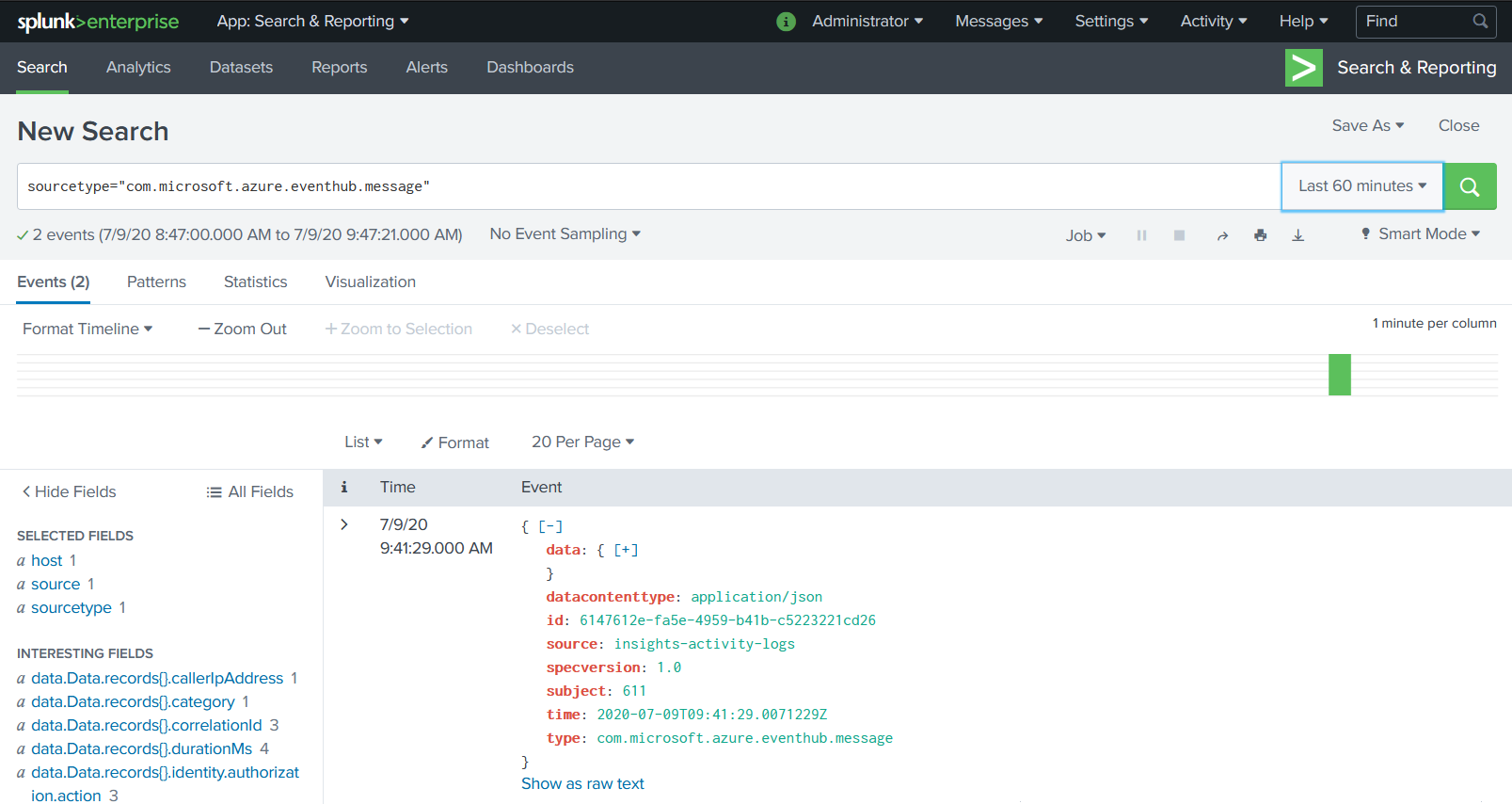
For more information about using Splunk, please refer to the Splunk documentation.